Isolation in Containers
This is achieved by using namespaces.
Even though Docker gives a feeling that containers are individual machines, it's not true.
It's just another process running with different set of namespaces.
Image Contents
The docker image contains it's own userspace rootfs filesystem. Meaning it contains it's own /bin, /lib, /usr, /etc file systems which are mounted into a new mount namespace.
Prepare Namespaces
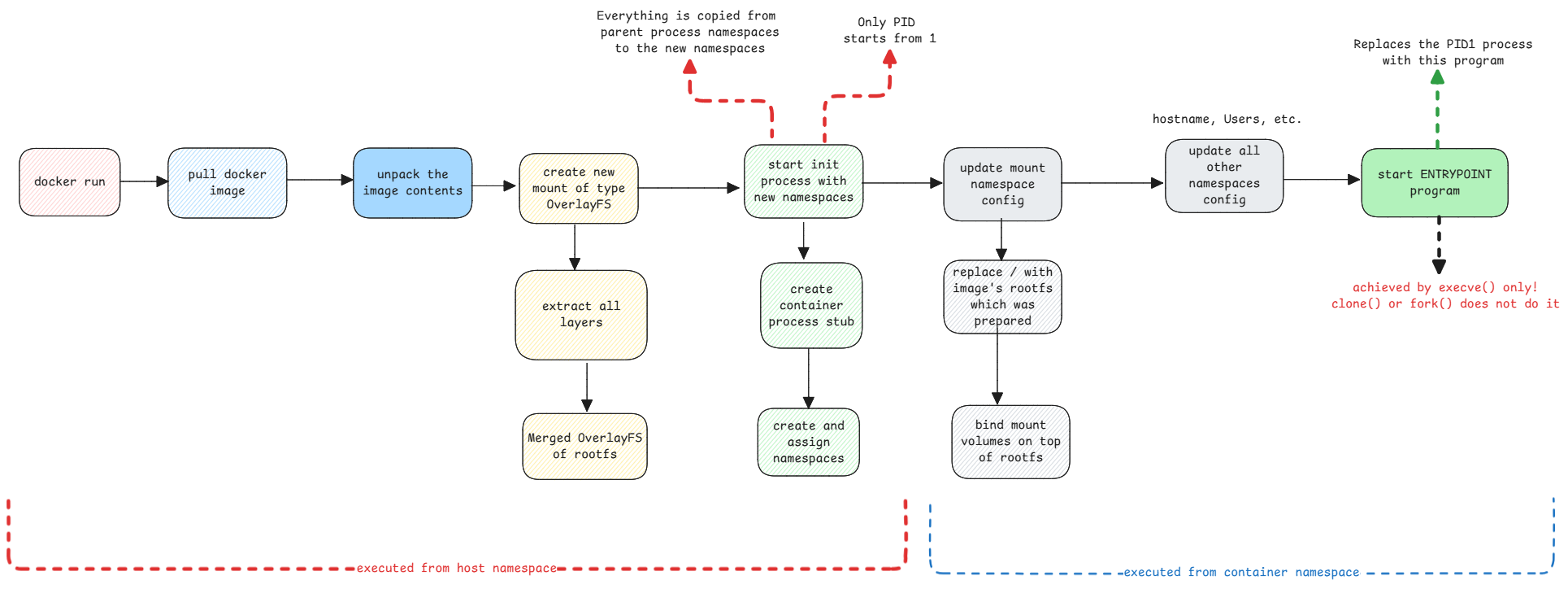
When a container is started, the docker binary first creates all necessary namespaces. These new namespaces will be a copy of the parent process's corresponding namespaces.
Then it will start the init process which then updates the namespace content accordingly.
clone() Method
Similar to fork() method of Linux, containers use the clone() method to start the process. The application process mentioned in the Dockerfile is started using this method.
This method provides an option to specific which namespaces are required to be created for this new process.
When we pass --network=host to the docker command, it will simply avoid creating network namespace.
kernel dependency
Since the containers doesn't have a kernel packaged inside, it can work only with a host that has a kernel for which the container is prepared for.
Even though it has it's own rootfs, all the system calls generated by the binaries in rootfs are handled by the host kernel.
Container Creation Process